Securing Video Conferencing: The Definitive Guide for 2024

Important Note
The information contained on this page is for general information purposes only.
Nowadays, people are dependent more on video conferencing for communication as remote work endures to succeed even beyond the COVID-19 pandemic. To be precise, the web conferencing market is estimated to reach 13.8 billion USD by 2023.
Therefore, building a secure video conferencing platform is a necessity to retain customers. Otherwise, users will leave the platform in droves, and companies will lose tons of business.
Enterprises are exploiting video conferencing software now more than ever. This way, customers, employees and clients can converse with each other for increased productivity and collaboration.
To secure your business, the following steps and practices will ensure utterly secure live video calls, anytime and anywhere.
Table of Contents
2 Non-Techy Security Standards to Support Video Conferencing
Captivating robust security features in the video calling solution is important. But before integrating that, there are a few other security standards to be aware of.
1. Vigilance of Employees
At times, the best security feature is in your employees’ habits and security training instead of your video conferencing solution. These habits of employees can go a long way to protect your company’s and customers’ data.
For small businesses, it may be tempting to relax on the security training. But on the longer run, it is one of your best first defenses in terms of cybersecurity.
2. Working in Public Places
Working in public places has become a lot more accessible. Thanks to mobile devices, however, it still carries its own risks.
It’s already a no-no if you’re using an open Wi-Fi or a public internet connection. They’re inherently less secure than private networks while it may seem convenient. This is because you can log on without having to enter a password. At least use a reputable VPN to protect your data while using Wi-Fi in public.
Encrypted Video Conferencing And Other Features To Look Out In 2024
If you start searching for video conferencing solutions, you might come across “End-to-End Encryption,” at some point.
End-to-end encryption or E2EE is not equivalent to a standard encryption or full encryption. Instead it’s a specific encryption that secures the data in online video conferencing software. Majority of video conferencing tools are not enabled with end-to-end encryption. But standard encryption is likely good enough as long as you’re not reciting bank account numbers on video meetings.
Ideally, your video conferencing tool must have additional security measures in place.
Any calls you make through the video conferencing platform, such as the in-transit web requests, are encrypted. It uses TLS and application data that is permanently stored at rest uses AES 256-bit within Google Cloud Platform. The platform also adheres to GDPR regulation for data protection of EU citizens and HIPAA compliance standards.
And there are other features within a video conference call that support to protect your platform from unwanted guests such as:

Ability to Boot Out Participants
If you don’t recognize the users who joined the conference line, you can promptly remove participants. Also, you can permit entry of participants with a single click.
Password or PIN
You can require a PIN for a video conference call as a security boost. Otherwise, you can also share the meeting link with your attendees to make them join easily.
Meeting Rooms
To keep your meetings secure, you can make the participants wait in a virtual meeting room. Later, you can allow them in once you enter the meeting.
Meeting Lock
The hosts can lock the meeting when everyone has joined the video conference, so that other uninvited guests cannot aimlessly join.
Muting Participants
The host will also be able to mute all participants for security measures or as a courtesy to whoever is presenting.
There are several things that will ensure a secure video conferencing experience for users. Nevertheless, these are the few best strategies for you to optimize web conferences for security.
Recommended Reading
3 Best Secure Video Conferencing Platforms/Software in 2024
The three most powerful secure video conferencing platforms are:
1. Signal – The Most Secure Messaging Software For Web & Mobile
2. Viber – A Modern Approach To Securing Conversations
3. LiveStorm – Safeguarding Meets & Webinars For Enterprises
1. Signal
“The Most Secure Messaging Software For Web & Mobile“
Signal is a popular messaging platform that uses end-to-end encryption to keep your chats and calls secure. This robust platform has built iron-clad security features to ensure that no user info or conversation is leaked or breached by potential vulnerabilities. Since Signal is an open source software, the vulnerabilities are fixed within days, unlike vendors who take longer cycles to release patches.
Why Is Signal Secure To Use?
- Lock pin
- End-to-end encryption of user chats, calls and account data
- Audio and video permissions
- Self-destructing messages
- Encrypted stickers
- Chat Archiving
Platform Compatibility: iOS, Android, Windows, Linux, macOS & more
Pricing: Free
2. Viber
“A Modern Approach To Securing Conversations“
Viber is a full-featured communication platform that has impressive messaging and calling features. Across any mobile or web app, you’ll be able to make 100% encrypted voice and video chats, leveraging a perfect communication experience.
Above this, Viber protects every conversation with a color-coded encryption display on each profile.
- Green – Trusted & Encrypted profile
- Grey – User Not Trusted
- Red – Authentication Error
Why Is Viber Secure To Use?
- End-to-End Encryption
- Delete Messages
- Color Coded Encryptions
- Block & Report
- Secret Chats
- Screenshot Protection
- Security Code
Platform Compatibility: Web & Mobile Apps
Pricing: Free
3. LiveStorm
“Safeguarding Meets & Webinars For Enterprises“
Amongst several messaging and video calling platforms, Live Storm is uniquely known for the security it offers to webinars, conferences and meetings. This cloud-based software provides a diverse variety of tools to help businesses like you manage and optimize your events/ meetings.
Plus, this software employs strict moderation controls with adherence to privacy regulations like GDPR and HIPAA, to protect its users
Why Is Livestorm Secure To Use?
- End-to-End Encryption
- Waiting Room
- Moderation Tools
- Event Passwords
- Privacy Compliances
Platform Compatibility: macOS, iOS, Android and Web browsers
Pricing: Livestorm offers 3 different pricing plans:
- Free: For up to 100 participants
- Pro: Priced at $99 for up to 500 participants
- Enterprise: Custom pricing
7 Steps to Ensure Secure Video Conferencing Platforms
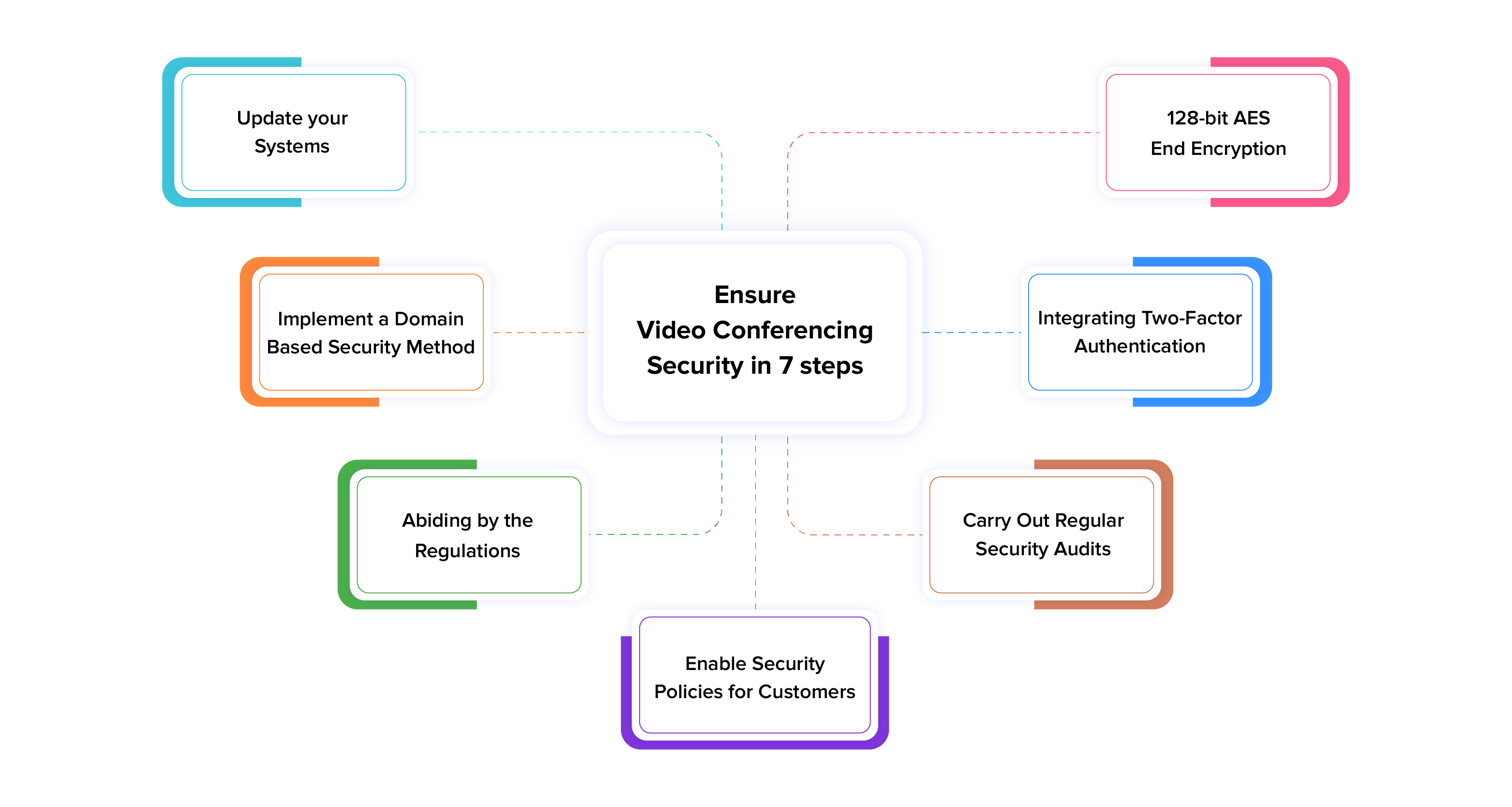
1. Update your Systems
Outdated systems are easy access platforms for the hackers. By exploiting the system’s weaknesses hackers enter your networks. They steal your customer data and sabotaging your platform or do whatever they need.
Hence, to combat any known cyberattacks that could harm your ecosystem, ensure to frequently update your software. Investing in the latest security secures to protect your data from any harmful threats.
2. 128-bit AES End Encryption
Data transfers through multiple public and private networks to reach users. That’s where 128-bit AES encryption comes into play to make the data transmission vulnerable to cyberattacks.
It secures the video conferencing platform to protect the shared data throughout their customers’ meetings. It enables encrypting and decrypting features for all video meetings to deliver robust security and thus avoid attacks from hackers.
3. Implement a Domain-Based Security Method
The video conferencing platform should possess an effective way for the hosts to block random participants from user’s video conferencing solutions. This may lead to an annoying experience for web conferencing users.
Business owners can offer the users with advanced permission settings with domain-based security tools. This will help moderators control the participants who enter the meetings or webinar. Therefore, to enter the upcoming web conference, participants will need obvious permission from the host.Consequently, users will have the liberty to communicate without any hassle by the intruders jumping in the call. You can also say goodbye to these frustrating “Zoom bombing” moments or any other such incidents that ruin online video conference systems.
4. Integrating Two-Factor Authentication
Two-factor authentication adds an extra layer of protection to your video conferencing platform. It ensures you to allow only invited participants to access the meeting rather than single sign-on (SSO) to web conferences.
For instance, before joining the conference it might oblige the users to receive a code via text. The hackers will have a hard time joining the video-calling meeting room, even if they already know the user’s sign-in info.
5. Abiding by the Regulations
With all internet regulations surrounding customer privacy, creating a secure video conferencing tool necessitates to be compliant. Below are the main rules that surround user data and what do it consisting of:
HIPAA: Health Insurance Portability and Accountability Act is a critical act ruling for companies in the telemedicine industry. It thus protects the patient’s medical information and records to stay secure and also sets limits over their transfers.
GDPR Compliance (General Data Protection Regulation): It is a regulation set by the European to protect the privacy rights of EU citizens. This rule will concern you if you have online video conferencing users across the states of the EU.
If you don’t abide by these regulations, it will not only put your users at risk. But also can subject your company to expensive penalties. Secure Video APIs guarantee high-level security by complying with all these regulations. This lets you focus on providing the best online conference experience for your users. It only takes a couple of lines of code, and you’re all set.
6. Carry Out Regular Security Audits
Business owners must ensure to continually run security audits for the platform and lookout for any suspicious activity. The sooner you spot the security issues, the better it is for the business video conferencing software.
Identify the weak spots during your security audit in the systems and find ways in which you can improve. Spend some time to educate your employees on cybersecurity issues and measures that they should initiate to preserve your platform secure.
7. Enable Security Policies for Customers
Another expert tip is to assist the users to make their online video conference rooms secure by delineating security policies. For instance,
- Reduce the sharing of data privacy in the course of conference calls.
- Immobilize cameras or microphones when it’s not in use.
- Avoid the usage of personal devices in virtual hangout
- Avoid screen-sharing sensitive information during group conferences.
In the course of video conference calls, these tips will aid users to create and secure boundaries. Also, it supports the users to deliver accountability and personal responsibility for their own safety.
How Can You Keep Your Video Conferencing Secure With MirrorFly?
MirrorFly’s video calling APIs come with strong encryption protocols like AES-256 and TLS/SSL mechanisms to protect data from any pirating eyes. Along with these, we are also compatible with industry regulatory standards like GDPR & HIPAA, ultimately making our SDK suite secure and sound.
In case you are ready to get started with us, please learn that MirrorFly offers two pricing options. The first is SaaS, a “Pay-as-you-go” model that gives access to Chat APIs and a free demo on video calls. The second model is the Self-hosted or SaaP solution that offers endless customizations, and a white label chat solution.
Build your own video conferencing platform right away!
Get Started with MirrorFly’s Modern Video Calling API!
Drive 1+ billions of conversations on your apps with highly secure 250+ real-time Communication Features.
Contact Sales200+ Happy Clients
Topic-based Chat
Multi-tenancy Support

Frequently Asked Questions (FAQ)
Secure video conferencing refers to the practice of conducting video meetings or conferences over the internet while protecting the privacy, confidentiality, and integrity of communications.
MirrorFly, Livestorm, Google Meet, and Microsoft Teams are popular choices for secure video conferencing software. They offer various security features, including encryption, authentication, and access controls, to protect sensitive information from unauthorized access.
To secure your video conferencing app, you need to follow the below practices,
- Always create a meeting ID and meeting password
- Whenever not using the meeting lock the meeting
- Never share video conferencing links unnecessarily
- Set-up your waiting room
- Allow screen sharing only when required alone
- Try to utilize the audio interaction more than video display
- Keep a track on live captioning with security
Encrypted video conferencing refers to the video calls that are protected with security protocols. It helps you keep your data safe from third-parties and reduces the risk of security problems.
The easiest way to secure your online meetings is to set a strong password for the meeting and share it only with the people you want to join. This helps keep unauthorized participants out and ensures that only authorized participants can access the meeting.
It completely depends on the specific video call app you’re using. Many video chat platforms like Zoom, Microsoft Teams, Google Meet, and Skype offer encryption, which means the video and audio data is protected. However, not all video call apps provide end-to-end encryption.
Yes, VoLTE (Voice over LTE) video calls are generally secure. Each call is transmitted over LTE (Long-Term Evolution) networks, which uses strong encryption to protect the call data. However, the level of security depends on the specific privacy standards set by the service provider.
Yes, video calls can be hacked if they aren’t secured properly. This means someone might eavesdrop on your conversation or access your calls without permission. To prevent this, you need to use secure apps, strong passwords, and be careful with sharing links and information.
Related Articles
- Communication APIs: Top 7 In-app Chat, Voice & Video APIs
- 9 Best Web Browser Video Chat for Building Video Apps
- How to Build A Flutter Video Call App in 2024?
- How to Build a React JS Video Chat App in 2024?
- How to Build an Android Voice and Video Calling App Using Java?
This is really a great article. I just started looking for secure video conferencing app and I feel like I have a better idea where to go from here. Thank you lot. keep writing
I am interested in your secure video conference solution for my business. We need your on-premise support and would love to receive a demo project so that we can discuss things internally with all the team members. Kindly contact me via email.
Hello Team, we would like to integrate the MirrorFly secure video conferencing software to our communication application like zoom. MirrorFly is one of the providers that we are looking into and would like to discuss more about its capabilities, customization and specific features.
Looking out for your secure video conferencing solution to our android app. I am building a video conference platform to connect healthcare providers to patients. Kindly let me know the pricing or packages you have. Thanks
Hi, we are developing video conferencing app and we found mirrorfly perfect choice for our secure video chat. I would like to know about the pricing for on-premise service, and the possibility of customized services pricing.
I want to use your secure video conferencing api for our both android and ios application healthcare project. I want to request a demo first. Thank you!
Thanks for sharing. Your blog is so amazing. It is a very helpful content for selecting best secure video conferencing platform.
I want to develop a secure video conferencing app for our healthcare app. I would like to seek your help to get started. can you please help me to decide technology stack for it?
I’m interested in your secure video conferencing solution for our app and website. Please share a demo, some development/integration guidelines and pricing details.
Looking for a secure video conferencing api for our e-commerce app. Kindly share me the details.
Video conferencing certainly is an expensive solution in current online market. Its a great to understanding the detailed concept of secure video conferencing. Thanks for sharing.
Looking for your secure video conferencing api & sdk solution. Needs to develop video conference app for ios, android & web application for my healthcare project.
Amazing Article. Thanks for sharing the major steps for secure video conferencing solution.
Dear Team, We have a medical platform and considering either to develop a secure video conference between practitioner/patient ourselves or purchase this feature. Would you be able to inform us if we can use your video facility within our platform and in which format. Please do let me know.
Thank you for this article. Are you using end-to-end encryption of this video conferencing api & sdk.
Thanks for sharing the best secure video conferencing solution. Keep sharing more interesting posts.
Hi, we would like to integrate an api for our application which requires video conferencing one to many and multiple interaction. Kindly send me the details through my mail id.
We are looking for video conferencing solution to integrate with healthcare app, kindly share me the pricing
We are providing online consultation of our doctors. Kindly share any demo project in healthcare.
I need to implement video conference and broadcasting in my healthcare project, can we get any documentation and SDKs of Mirrorfly for video conference and broadcasting functionality.
Hi we are looking for secure conference video chats for android/iOS native platforms. Interactive with more than 6 users. Do you have any samples?